The last article introduced GitHub SSH Access Enhancement with FIDO2 Security Keys (yubion.com), yet it did not cover whether FIDO security keys for SSH access can be used in non-GitHub environments.
With the new features in OpenSSH 8.2, users of all Linux servers (Ubuntu, Debian, CentOS, Fedora, etc.) can now use FIDO security keys in SSH. This article will introduce SSH access to Linux servers using YubiKey.
Environments :
OS: Linux Ubuntu 20.04 (client and server)
YubiKey 5 NFC
SSH Access Configuration:
SSH key pair generation and use are similar to standard usage
1. Plug the YubiKey into the USB port.
2. Open a terminal and enter the following command to generate an SSH key.
sk refers to Security Key
$ ssh-keygen -t ed25519-sk
Note: If the command fails and an "invalid format" or "feature not supported" error is displayed, the security key used may not support ed25519. Try ecdsa instead of ed25519.
The YubiKey 5 NFC firmware used this time is 5.1.2, so it cannot generate ed25519 keys, so ecdsa keys are generated instead.
To use the Ed25519 key, please use YubiKey firmware 5.2.3 or later.

Checking YubiKey firmware with YubiKey Manager
3. Enter the FIDO2 PIN for the YubiKey and touch the key.
4. When "Enter a file in which to save the key" is displayed, press Enter to save the public key to the default file location.
5. Create a password for the public key file.

Example of SSH Key Generation
6. Copy the SSH public key from the generated "id_ecdsa_sk.pub" file and add it to the "~/.ssh/authorized_keys" file on the server to be connected to.
SSH Access with FIDO Security Key:
1. Insert the YubiKey into the USB port.
2. Then, open a terminal to access the server.
$ ssh user@server_ip
3. Enter the password of the private key file and touch YubiKey.

Example of Accessing Server
If the above screen is displayed, it indicates that the setup of SSH access using the FIDO security key as two-factor authentication like with GitHub was successful.
4. Also, to log in without a password, check the "Automatically unlock this key whenever I'm logged in" checkbox to require a password only upon the first log-in.
Disabling User and Password Only Login :
1. Run the command on the remote server to edit the SSH daemon configuration file.
$ sudo nano /etc/ssh/sshd_config
2. Uncomment the "#PasswordAuthentication yes" line and change it to "no" to look like the screenshot below.
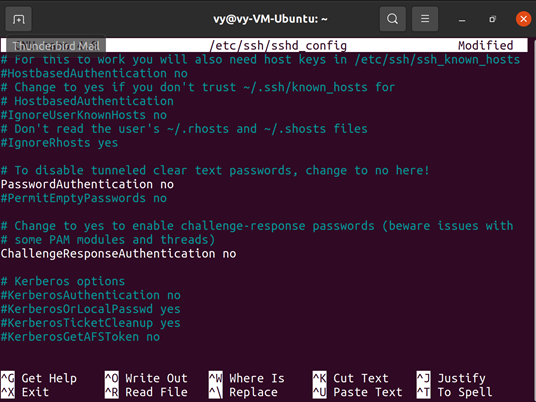
Example of SSH Daemon File Configuration
3. Press Ctrl + X (to finish editing), type "y" (to confirm file save), and press Enter (to confirm file name) to save the file.
4. Finally, reload SSH.
$ sudo systemctl reload ssh
Then, when connecting to the server without the FIDO security key, the following error message will be displayed.


Example of an Error
Conclusion:
This article introduced SSH access to Linux using YubiKey, through which users can store their private key in a hardware security key and operate a simple, secure two-factor or single-factor authentication.
However, since the OpenSSH version for Windows 10 is still 8.1, clients cannot use FIDO security keys on Windows 10.
Instead, YubiKey's PIV function to "Manage SSH private keys with YubiKey on Windows (yubion.com)" can be used.

